Anyone one who knows me or reads my blog can be certain of one thing. I like SonicWALL products. The company's product line is growing and maturing so fast it is incredible. This growth charge is being lead now by the Enterprise Class firewalls or E-Class as they are known. These products are changing the landscape and have raised the bar in performance and throughput. There is not another enterprise class product on the market that can do what the E-Class firewalls do. When you consider the price, the E-Class is by far the best value for the dollar.
I have to say that working with churches is always an honor. I just completed a job for Willow Creek Community Church, a church known not just here in the United States but worldwide for it's service to Jesus Christ. Having been given the trust of a church of this size and stature in the ministry is nothing less than a true God thing. Kudos to Kurt Donnan and his team at Willow Creek for the opportunity.
The project was to replace their SonicWALL Pro 4060 which has been in service for about three years. It currently has a 45 Meg connection via a DS3 and was pretty much at its limit handling what the Willow network was throwing at it. The replacement for the Pro 4060 was to be a pair of brand new E-Class NSA 6500 Firewalls. They were to be installed in a High-Availability pair to not only upgrade the capability at the head end of the network but to also add a layer of redundancy as the previous install was a single point of failure for the network.
Now, as anyone who has cut over the gear connecting a big network to the Internet knows, this can be a nightmare for the users if the project is not well thought out and carefully executed. Down time is never really acceptable and can ultimately create a black eye for the IT department of any network. This was no different at Willow Creek. Fortunately, SonicWALL made this process much easier by allowing the content rules and programming of the Pro 4060 to be importable into the new E-Class. I was not about to take for granted that this would work smoothly so Kurt, myself, and his team all diligently reviewed every rule, process, and custom bit of configuration that was imported to the E-Class device. When done the only thing we found is that some orphaned firewall rules that really should have not been in place on the Pro 4060 were successfully cleaned up and purged from our new configuration. That was the first sign things were really headed in the right direction. We went ahead and shut down the Pro 4060 and lit up the E-Class box to the production network. The outbound connections all came up with no issues at all. As we audited inbound traffic we noticed that connections were not being made. My suspicion was that some NIC's were not happy about the hardware change in real time and mid-stream. I simply rebooted the E-Class gear and the servers that were not communicating. Every single connection came online and worked flawlessly. Total time from Pro 4060 shutdown to E-Class NSA 6500 assuming all network functionality was less than 10 minutes. For the end uses at Willow Creek the change was totally transparent. The quote was "It can't be that easy. This was the easiest cut-over we have ever done." I really can't take the credit here. Kudos to SonicWALL and the engineers that developed the NSA E-Class products. They are simply awesome!
Post conversion I thought we should test the new install performance. The inbound connection is 45 MB over a DS3 so we should have been able to get the E-Class to show us some real use with the network in production. Here is a snapshot of the E-Class on a Monday just after conversion with podcasts, credit cards, browsing, email, downloads, and everything else going on.
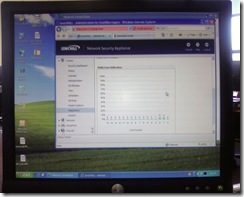
Can you say yawn? Only 2 CPUs were in process! To be fair it was later in the day but we still thought there would be more load then that. This was with all the UTM (Unified Threat Management) turned on. To just push the issues we decided to max out the DS3 with 7 simultaneous downloads of Vista SP1, several video streams, -t pings to outside servers, etc. The graph of the DS3 showed it right at the top of its inbound limit. Below is the graph of the E-Class CPU graph.
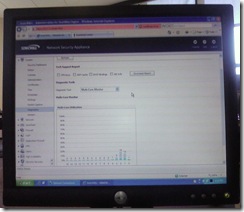
We managed to get 5 CPUs engaged. CPU 2 actually got to 41% for a brief second but I could not snap the photo quickly enough. When we ran this test we had already installed the second E-Class for a High Availability fail-over. We pulled the plug on unit one and the only thing we lost on all the stuff that was running was one ping at about 30 ms.
The E-Class boxes are a great product. If you have a Cisco, Juniper, Fortinet, Watchguard, or any other firewall solution or are looking to make a change, contact Willow Creek and see what they think. I think they will tell you to give the E-Class some serious consideration. In the ministry space as well as any other market there is no other product that can come close to providing top value for the ever shrinking IT dollar.
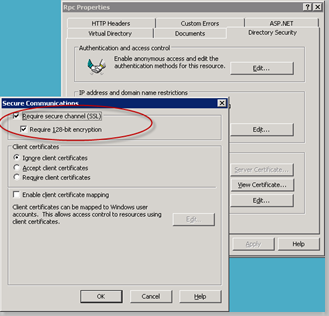
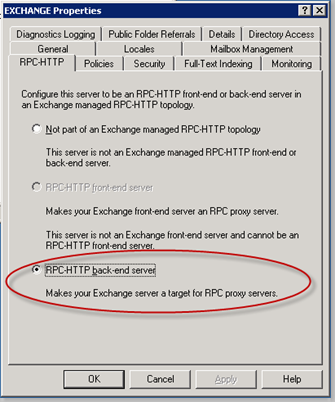 Select RPC-HTTP back-end server. Click OK and close the MS Exchange System Manager.
Select RPC-HTTP back-end server. Click OK and close the MS Exchange System Manager.